
10 Aug 2025 - David Rupprecht
⌛ TL;DR: By 2026, all critical components in Germany’s 5G networks must be certified. This complex, time-consuming process requires vendors to start early to meet the deadline. Uncertified critical 5G equipment can’t be deployed in public networks. Need help getting started? Contact us at info@montsecure.com
Beginning in 2026, Mobile Network Operators (MNOs) will be mandated to deploy only certified critical components in public 5G networks in Germany. Consequently, vendors of 5G network equipment must ensure their products comply with relevant certification schemes. In this article, we will clarify the complex landscape of requirements and certifications. We will explore the scope of certification and the associated certification process. What products are impacted? How does the certification schemes work? What are implications for MNOs, vendors, and certification centers?
Which 5G products require certification?
According to the TKG (Telecommunication Act), critical components must be certified by a recognized certification body before their first use. Figure 1 provides a high-level overview of all relevant documents and their issuing institutions. It’s worth noting that most of these laws and policies stemmed from discussions beginning in 2018 regarding the trustworthiness of certain vendors.
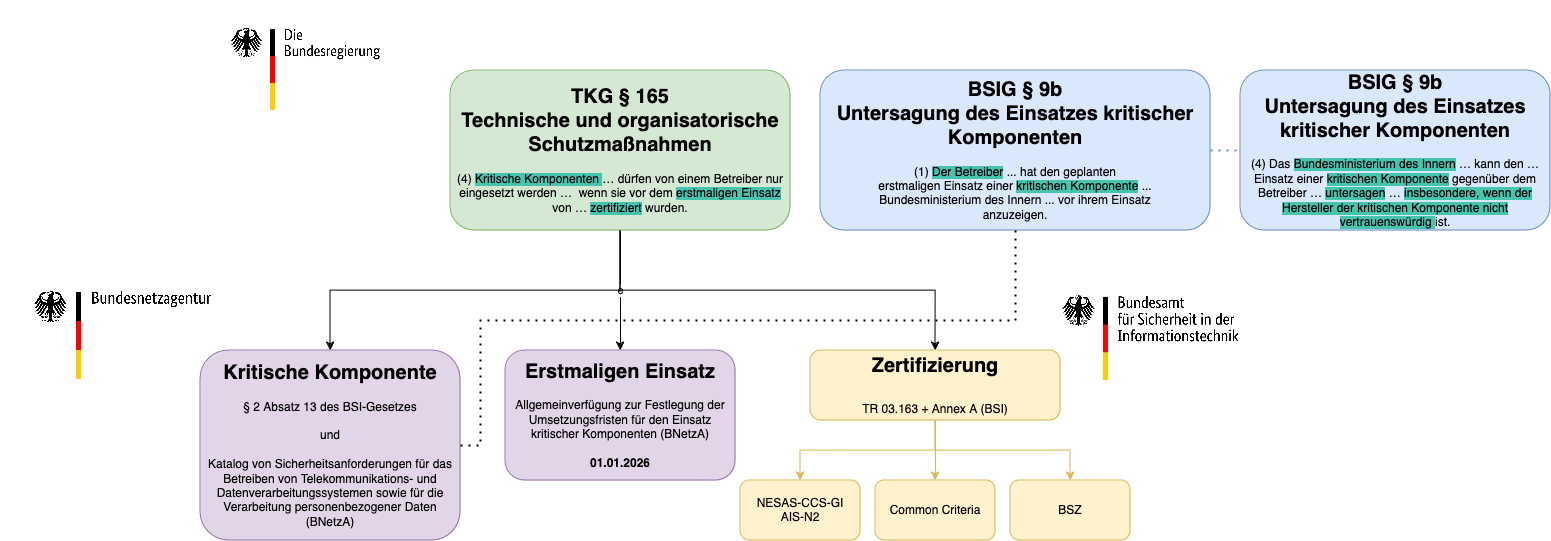
Figure 1: High-level overview of all relevant documents and the issuing institutions
What are critical components?
Let’s explore which products require certification. The answer can be found primarily in the BSI-Act and a document by the Bundesnetzagentur (BNetzA), respectively.
Legal definition of critical components in 5G networks
The BSI-Act provides a comprehensive definition of critical components in the context of information technology and infrastructure. According to the act, components are broadly defined as software, hardware, and any interconnected elements that process information using IT. The act further specifies critical components as those used in critical infrastructure where disruptions to their availability, integrity, authenticity, or confidentiality could lead to significant impairment of critical infrastructure functionality or pose threats to public security. Additionally, critical components are those either explicitly designated as such by law or those that perform functions deemed critical based on legal provisions. This definition underscores the importance of identifying and securing components that play a crucial role in maintaining the stability and security of critical infrastructure systems.
Guidelines for identifying critical components in 5G networks
As these legal definitions are somewhat abstract and lack concrete guidelines, BNetzA provides a much clearer framework for determining whether a product requires certification. It defines critical functionalities, from which the criticality of the underlying software or hardware component can be derived based on whether it (partially) performs these functions. These functionalities are outlined in Table 1.
This requirement is non-negotiable for core network functions (Category a) and for NFV management and network orchestration (Category b). For Categories c) through f), exceptions may exist, but a strong justification must be provided to argue that the component is not critical.
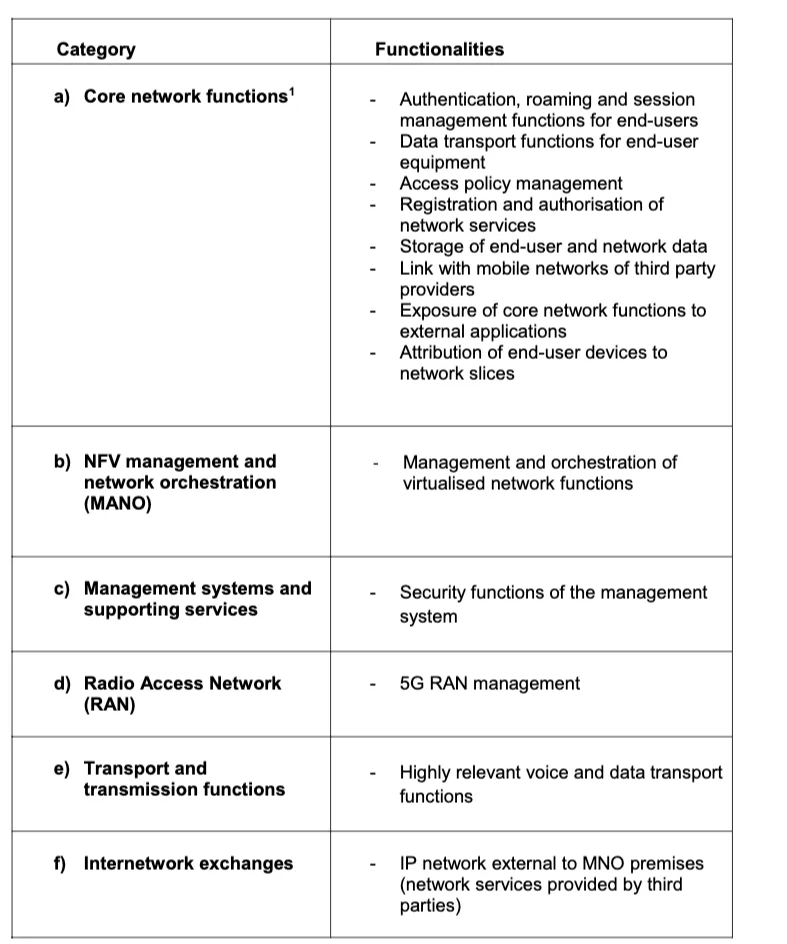
Table 1: List of critical functions for the 5G network
The list encompasses all the essential elements required to operate a 5G network, including core network components, virtualization, management, and transport functions. Interestingly, only RAN management is classified as critical under the RAN category, while the RAN itself (such as base stations and gNodeBs) is not considered critical.
How is a 5G product certified?
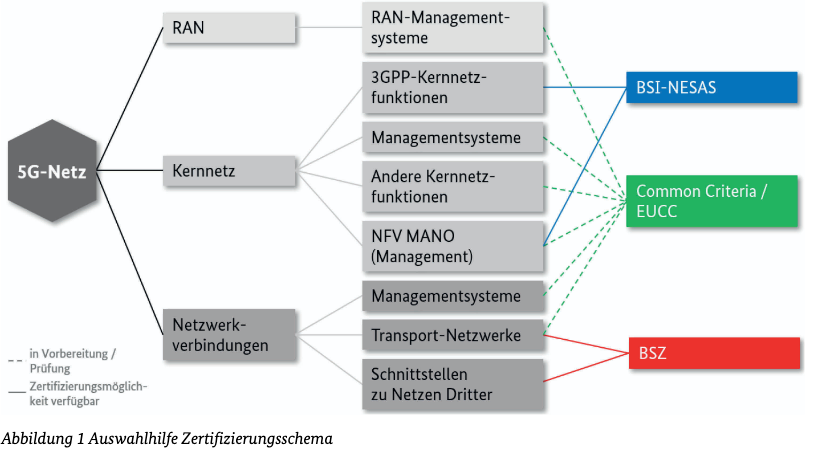
While we now understand what requires certification, the next question is how to certify it. This responsibility falls under the BSI’s domain, with BSI TR-03163 outlining the technical approach. In general, three certification schemes are applicable: Common Criteria, BSZ (Beschleunigte Sicherheitszertifizierung), and BSI NESAS. Annex A of BSI TR-03163, Guidance for Choosing a Certification Scheme and Approved Requirements Documents, provides a helpful overview for selecting the appropriate scheme for each component.
As illustrated in TR-03163 Annex A, all 3GPP-defined functions must be certified using the BSI NESAS scheme. Management and virtualization functions fall under the scope of Common Criteria certification, while the BSZ scheme is intended for transport networks, such as switches and routers.
What is the deadline for certification?
Let us recall that the Telecommunications Act mandates that all critical components must be certified prior to their first use.
The question now arises: what is meant by “first use”? This is a timely issue, as MNOs will not be able to update or deploy new equipment on their networks unless it is certified. The deadline for certification is set for January 1, 2026, as defined by the Bundensnetzargentur in the document General Ruling Establishing the Implementation Deadlines for the Use of Critical Components (can be found here).
The deadline for the respective critical component is the last day of the 24th month after certification of the product to which the respective critical component belongs is first possible in accordance with TR-03163 of the BSI, but no earlier than 01.01.2026.
“First use” refers to when a device is introduced into the network for the first time. This includes the following scenarios:
-
The MNO introduces a new type of component into the network. For instance, if the MNO does not deploy an AMF until January 1, 2026, but begins rolling it out on or after this date, the AMF must be certified.
-
The MNO deploys another instance of an already-used component with the same version in the network. If the MNO has three AMFs running in the network by December 31, 2025, and wants to scale by adding a fourth instance after January 1, 2026, this new instance must also be certified, even if it is from the same manufacturer and is the same version.
-
The MNO upgrades to a new version of a component across all instances. If all AMFs are running version 1.0.0 by December 31, 2025, and the MNO wants to install version 2.0.0 starting January 1, 2026, version 2.0.0 of the AMF must be certified.
These stringent requirements for MNOs directly translate into requirements for vendors of 5G equipment. As of now, vendors have less than 20 weeks to certify their network equipment!
Let’s create a secure 5G together.
The certification process is time-intensive, making it crucial for vendors to start integrating all necessary processes into their development workflows as early as possible.
However, by the start of 2026, only certified network equipment will be permitted in German 5G networks. It is crucial that we collaborate to meet this deadline and ensure the timely deployment of 5G networks without delay.
With our easy-to-use solution, SEAL, you can test your 5G product against the necessary security requirements defined by the BSI NESAS. SEAL helps you achieve certification much faster and significantly reduces overhead. We are happy to assist you in setting things up. Feel free to reach out: info@montsecure.com.